What is a Log File?
A log file is an event that took place at a certain time and might have metadata that contextualizes it.
Log files are a historical record of everything and anything that happens within a system, including events such as transactions, errors and intrusions. That data can be transmitted in different ways and can be in both structured, semi-structured and unstructured format.
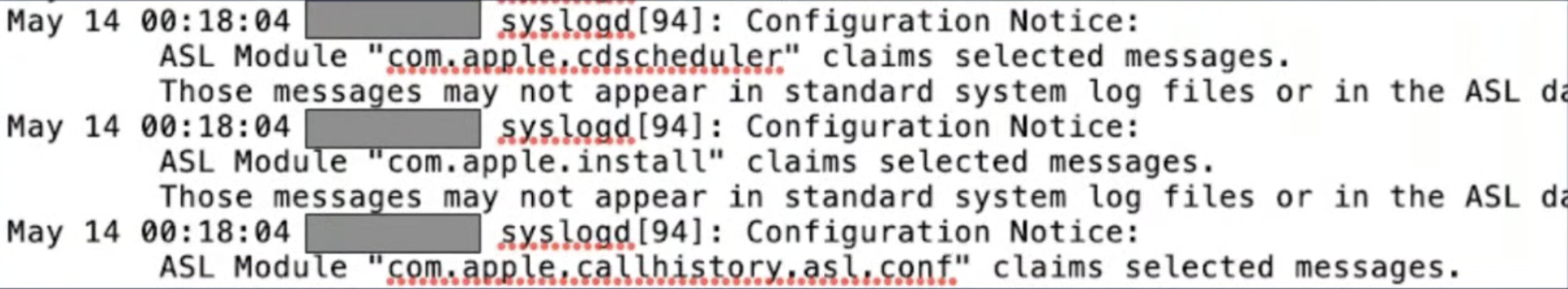
The basic anatomy of a log file includes:
- The timestamp – the exact time at which the event logged occurred
- User information
- Event information – what was the action taken
However, depending on the type of log source, the file will also contain a wealth of relevant data. For example, server logs will also include the referred webpage, http status code, bytes served, user agents, and more.
Where do Log Files Come From?
Just about everything produces some version of a log, including:
- Apps
- Containers
- Databases
- Firewalls
- Endpoints
- IoT devices
- Networks
- Servers
- Web Services
The list goes on, but the point is, almost all infrastructure that you interact with on a daily basis produces a log file.
Who Uses Log Files?
Log files can provide almost every role at an organization with valuable insights. Below are some of the most common use cases by job function:
ITOps
- identify infrastructure balance
- Manage workloads
- Maintain Uptime/Outages
- Ensure business continuity
- Reduce cost and risk
DevOps
- Managing CI/CD
- Maintain application uptime
- Detect critical application errors
- Identify areas to optimize application performance
DevSecOps
- Drive a shared ownership on application development and security
- Saving time/money and reputational risks by finding potential issues before deployment
SecOps/Security
- Uncover clues around the ‘who, when, where’ of an attack
- Identify suspicious activity
- See spikes in blocked/allowed traffic
- Implementing the methodologies such as the OODA Loop
IT Analysts
- Compliance management and Reporting
- OpEx and CapEx
- Business Insights
Types of Logs
Nearly every component in a network generates a different type of data and each component collects that data in its own log. Because of that, many types of logs exist, including:
- Event Log: a high-level log that records information about network traffic and usage, such as login attempts, failed password attempts, and application events.
- Server Log: a text document containing a record of activities related to a specific server in a specific period of time.
- System Log (syslog): a record of operating system events. It includes startup messages, system changes, unexpected shutdowns, errors and warnings, and other important processes. Windows, Linux, and macOS all generate syslogs.
- Authorization Logs and Access Logs: include a list of people or bots accessing certain applications or files.
- Change Logs: include a chronological list of changes made to an application or file.
- Availability Logs: track system performance, uptime, and availability.
- Resource Logs: provide information about connectivity issues and capacity limits.
- Threat Logs: contain information about system, file, or application traffic that matches a predefined security profile within a firewall.
The Importance of Log Management
While there are seemingly infinite insights to be gained from log files, there are a few core challenges that prevent organizations from unlocking the value offered in log data.
Challenge #1: Volume
With the rise of the cloud, hybrid networks, and digital transformation, the volume of data collected by logs has ballooned by orders of magnitude. If almost everything produces a log, how can an organization manage the sheer volume of data to quickly realize the full value offered by log files?
Challenge #2: Standardization
Unfortunately, not all log files follow a uniform format. Depending on the type of log, the data may be structured, semi-structured or unstructured. In order to absorb and derive valuable insights from all log files in real-time, the data requires a level of normalization to make it easily parsable.
Chalenge #3: Digital Transformation
According to Gartner, many organizations, especially midsize enterprises and organizations with less-mature security operations, have gaps in their monitoring and incident investigation capabilities. The decentralized approach to log management in their IT environments makes detecting and responding to threats nearly impossible.
In addition, many organizations rely on SIEM solutions that are limited by cost and capability. SIEM licensing models are based on the volume or velocity of data ingested by the SIEM often increase costs for the technology, making broad data collection cost-prohibitive (although many log management tools have similar pricing models). In addition, as data volumes grow, SIEM tools might experience performance issues, as well as increasing operations costs for tuning and support.
Discover the world’s leading AI-native platform for next-gen SIEM and log management
Elevate your cybersecurity with the CrowdStrike Falcon® platform, the premier AI-native platform for SIEM and log management. Experience security logging at a petabyte scale, choosing between cloud-native or self-hosted deployment options. Log your data with a powerful, index-free architecture, without bottlenecks, allowing threat hunting with over 1 PB of data ingestion per day. Ensure real-time search capabilities to outpace adversaries, achieving sub-second latency for complex queries. Benefit from 360-degree visibility, consolidating data to break down silos and enabling security, IT, and DevOps teams to hunt threats, monitor performance, and ensure compliance seamlessly across 3 billion events in less than 1 second.


